Madison Duong





With technology evolving, entities have been gathering large volumes of personal data about users, mostly from websites, mobile applications, and web services. While many of these practices enhance the user experience and allow companies to customize their products and services, they also present significant privacy risks. Names, addresses, browsing history, and biometric information are stored in databases that can draw in hackers. Without strong protective measures, private information about a user can fall into the wrong hands, and identity theft, financial fraud, and covert observation can occur.
Organizations holding information about users implement security controls such as encryptions, multi-step verification, and data anonymization to counter such vulnerabilities. Yet, security breaches take place due to weaknesses in password protection, the presence of legacy software, and the activities of insiders in the organization. Furthermore, organizations commoditize user data for profit, often exchanging it with third parties for value, even without the user's consent. These activities raise ethical questions about transparency and people’s rights. These called for greater regulation and accountability of corporations. Regulations like the GDPR and CCPA have been passed, making users the owners of their data.
One key example of these privacy risks in information gathering is the case of Facebook-Cambridge Analytica. In 2018, it was made public that Cambridge Analytica collected data on millions of Facebook users in a way not consented to by them, and it used such data to influence political elections. The incident sparked a global discussion about the management of information, and it led to greater regulatory attempts and demands for more protective measures by corporations as far as their data is concerned. It highlighted the possible stakes that come with the unregulated gathering of data and the necessity of responsible management of information in contemporary society.

Computing resources such as servers, networks, and personal devices are an integral part of computer operations but are exploited for criminal purposes/ These resources are employed by cybercriminals through different methods, one of which is crypto jacking-a criminal operation that includes unauthorized cryptocurrency mining disrupting system performance-and DDoS attacks, which overwhelm the servers intending to bring down operations. Secondly, phishing attacks serve as a method of exploiting individuals to reveal secret information; this leads to security compromises and unauthorized access. These compromises go on to put personal security at risk, causing organizations and institutions to suffer significant losses, loss of confidence, and financial losses.
To deal with the exploitation of computer resources, there needs to be some form of corporation and individual-level cybersecurity measures put in place. Firewalls, intrusion detection, and updated security software make unauthorized access to the networks very difficult. Access is only allowed to certain people, and strong access controls with multi factor authentication permit access to sensitive resources. Government agencies and institutions have made new laws like the Computer Fraud and Abuse Act, CFAA, used in prosecuting computer hackers and, therefore, help protect computer resources.
An example of a well-publicized incident regarding recent cyber attacks is the Mirai Bonet, which was in 2016. Mirai malware infested hundreds of thousands of IoT devices, indicating an urgent call to revisit security issues on cybersecurity measures that may be relevant to consideration. In addition, the hack brought out the vulnerability of smart and networked devices and reminded the manufacturers of these devices that their devices needed to be designed with security considerations.

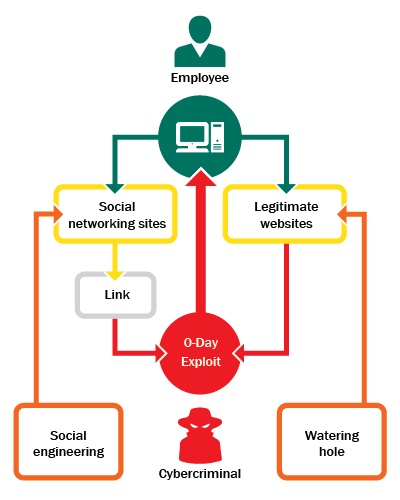
Attackers and malware compromise systems through social engineering attacks, malware, and brute-force methods. While social engineering forces users through psychologically manipulative techniques to disclose sensitive information, malware secretly records data from the infected computer in the form of Trojan horses of keyloggers. Poor password habits and unpatched security holes are common means by which the criminal finds easy ways of reaching the databases and compromising personal and organizational information. To prevent these types of attacks, cybersecurity specialists employ many kinds of protective measures.
In this respect, sensitive information is locked against unauthorized access through encryption, while MFA extends security beyond mere passwords. These regular timed software updates patch several kinds of weaknesses and hence reduce the chances of their exploitation. That is because it does the penetrating testing itself, performed by ethical hackers simulating the attack and finding those vulnerabilities while patching up a system. On top of everything, more sensitive sectors handle particularly sensitive data intended for confidentiality in all respects that shall be regulated through strict norm compliance, HIPAA, and PCI-DSS for those respective branches One of the best-known examples that epitomizes after-effects due to unauthorized access is the 2015 Equifax data breach incident.
The breach came about because hackers took advantage of a hole in the software not being patched; sensitive information like Social Security numbers, birth dates, and 147 million financial records were accessed. The incident caused widespread destruction of finances apart from ruining Equifax’s reputation, which came under subsequent legal action and investigations launched by different governmental agencies. The breach highlighted proactive steps required in cybersecurity and demonstrated an organization’s liability to maintain user data protection to its best possible shape.
Technological advancement has enhanced efficiency, communication, and problem-solving abilities across various domains. Artificial intelligence aids better medical diagnosis, cloud computing facilitates working remotely, and blockchain technology ensures secure electronic transactions. These innovations bring greater efficiency and higher living standards while portraying the revolutionizing effect of contemporary computing. They also, however, generate unexpected weaknesses like incursions into individual privacy, ethical issues, and cybersecurity risks. While technology is evolving, striking a balance between innovation and responsible usage continues to be a fundamental dilemma. One of the biggest ethical issues of technological advancement entails prejudice in artificial intelligence uses.
AI learns from big datasets, and if the datasets are prejudiced, then AI can unconsciously propagate bias. For instance, biased hiring algorithms can favor one community over another, leading to unequal hiring practices. Similarly, face-scanning technology has also been criticized for being susceptible to misidentification, particularly people of color, and undermining individual privacy and misuse by security and intelligence agencies. That, however, requires more innovative development of AI algorithms and greater transparency in the workflow applied during AI development. One possible pragmatic example today is where one might analyze the pros and cons of computer advances in deepfake technology.
Artificial Intelligence-driven deepfakes create realistic videos that can impersonate real people; what is more, they provide novel storytelling and entertainment options. However, deepfakes have been misused for all kinds of things, from disinformation to fraud and identity theft, raising concern for trust and security issues in the virtual world. Hence, governments are working on developing tools with technology companies to detect deepfakes to prevent their illegitimate use. This is the double-edged sword of technology development: it provides novelty, but at the same time, it brings ethical challenges and regulatory measures to prevent possible harm.